Back in September, I purchased the Robo & Kala 2 in 1 Laptop. I was looking for tablet that specifically ran Windows. Unfortunately, Windows tablets are few and far between, and those that exist are quite underpowered. That’s not to say that this device is a powerhouse, and we’ll talk about that more in a moment. But I was about to travel internationally for the first time in many years, and I was looking for a laptop that met two important requirements: battery life, and lightweight.
Continue reading “Robo & Kala 2 in 1 Laptop Review”Category: Computing
Gaining Command Prompt access on a Windows Computer that has never been set up
I sometimes work in an environment that has reasonably tight security requirements. One of those requirements as that a device’s MAC Address / Hardware Address be entered into a table on the router before it can be assigned an IP address.
I recently showed up on site with a brand new in box Surface Pro 9, but I had no idea how to get the MAC Address of the device because I could not log in and open a command prompt. Or so I thought.
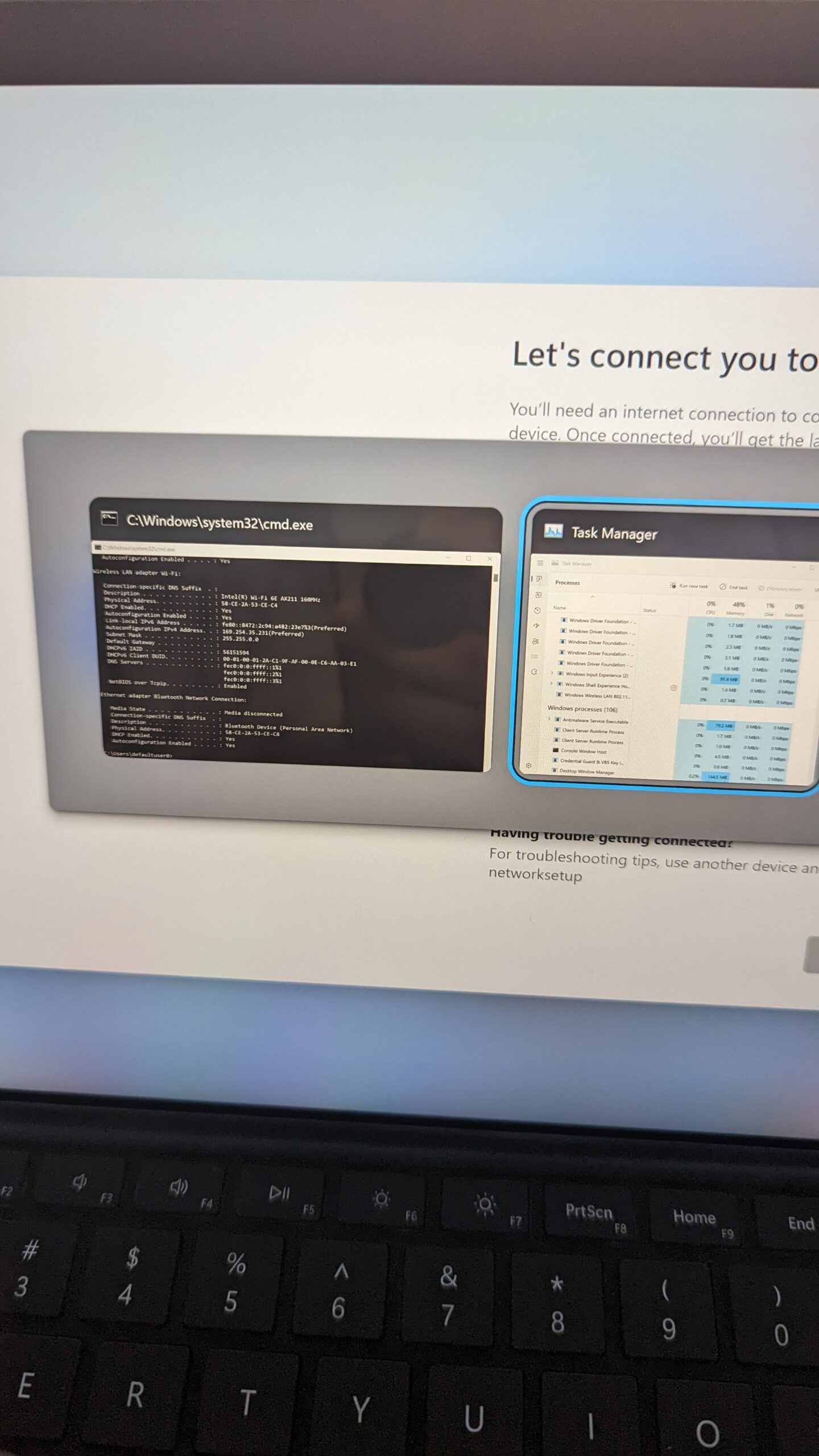
I got to the wifi screen telling me to create a connection, then pressed “Control+Alt+Escape” which brings up Task Manager. Although it did not appear on my screen, I suspected it was running behind the overlay locked to the forefront of my screen. I pressed “Alt+Tab” and was able to confirm my suspicion. I then used the keyboard combination of “Alt+F” to open the file menu, pressed Enter knowing that “Run” was highlighted, typed “cmd” and pressed enter to open a Command Prompt window. All of this was happening behind the “Let’s Connect You to a Network” screen, but as veteran of the keyboard era of Windows, all of this was second nature to me.
From there I was able to run the familiar ipconfig /all command, then, with the help of my phone’s camera, I could take a photo of the output of the command prompt and see the MAC Address that I was looking for.
This was convenient enough, but the thought of just being connected to wifi without ever logging in to the machine and then being able to take advantage of this “defaultuser0” account to open a terminal, and then utilize wget to download and execute potential malware before the computer has ever even been set up… fascinating. I’m sure this isn’t “breaking news” to anyone, infact the feature is probably left in, intentionally, for cases just like my original issue! But it does force me to take pause and think of what I can do with this.
Windows 10 / 11 HEVC Video Extension for Free
Microsoft offers the HEVC Video Extension necessary to play videos from iPhone users on their store, but they often try to charge a dollar for it. Just $0.99, in fact! In many cases, I don’t mind spending a dollar, and I encourage others to do the same. But sometimes you’re just in a pinch and you don’t have your credit card on file, or you aren’t logged in to your normal Microsoft account and it’s just a pain.
Have no fear! Microsoft also provides a link in the Microsoft store where you can download the HEVC Video Extension completely free of charge.
Why are there two, and why does this link exist?
Continue reading “Windows 10 / 11 HEVC Video Extension for Free”Apple is blowing it with this charging port fiasco

I’ve never been much of an Apple guy. The only Apple product I’ve personally owned was a used Mac Mini that I bought just so I could be a little more knowledgeable about helping people troubleshoot Mac problems. But when the European Union said that Apple had to ditch their custom charging port and make it “Common Charger” USB-C port, I feel like Apple missed a golden opportunity.
Continue reading “Apple is blowing it with this charging port fiasco”