File-Count Audits are a necessity in modern computing and security. Any number of security and auditing tools will automate this process for you, and notify you of discrepencies, but even the smallest IT firms can easily perform this task by hand with a simple search application. First, let’s discuss why.
Recently, companies as large as LexisNexis had their networks compromised by files that could’ve been anything from remote access trojans to botnet zombies. One article on Slashdot mentions that a file named nbc.exe was placed on the servers and resided there for months. Months!? Really? Nobody caught that? The file name is obviously suspicious, but not once did it come up in an audit of new files? People fall for “system.exe” or “OS.exe” or “Windows.exe” all the time – but to have a corporate server with a file named nbc.exe and nobody to take a second glance at it is quite poor.
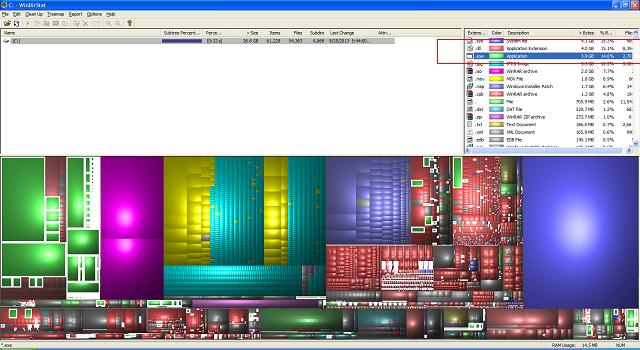
I get it, some companies have extremely large datasets. Auditing every little change might be practically impossible, or at the very least, excruciatingly expensive (both in terms of financial and system resources!). Still, even when the data you house changes, it isn’t typically going to be executable data. This is an easy thing to spot! Even free tools like the one shown above, WinDirStat, can be used to keep a running count and list of .exe files on your server. Your .exe filecount should practically never change, particularly without your knowledge. Some Windows Update installers / uninstallers might include new .exe files, but typically your server isn’t in a position to have the active number of executable files in flux.
Say you even have User directories on your Active Directory server, and a user uploads a .exe file into their directory. You still have no reason not to audit the contents of those directories, and perhaps enforce a security policy that executables cannot be stored on the server.
Performing a file-count audit once a month, even if it is just of critical filetypes such as .dll, .exe, and .bat; simple behaviors like this can protect you in the long run. Even if you don’t know every file name in every folder, just get a count of how many .EXE files there are, and if that number changes without you doing something, then you can pull the list of executables. Even with nothing to compare it to, I would hope a name like “nbc.exe” would jump out, particularly if it were in a nested folder where nobody would normally place a file. Use common sense and protect yourself, your company, and your customers.